2024-TSCTF-J-partWP-crypto
2024-TSCTF-J-partWP-crypto
出了五道入门密码题,非常荣幸,写一下题解。
ezRSA
1 | |
板子题,维纳攻击,Rabin,pq异或剪枝,coppersmith已知部分m
具体的都可以在网上找到非常非常详细的解释,这题确实也是为了让大家学会搜索而出的题目。
1 | |
ezNumberTheory
数论题说一说。
1 | |
part1
$gift+p = (p+q)^q \text{(mod n)}$
$gift+p = p^q+q^q \text{(mod q)}$
$gift+p = p^p \text{(mod q)}$
根据费马小定理我们知道
$p = p^p \text{(mod q)}$
$gift + p = p \text{(modq)}$
$gift = kq$
$q = gcd(gift,n)$
得q易解
part2
$gift = (n-1)^m\text{ mod(n*n)}$
$gift = (-1)^m\text{ mod(n)}$
代入发现
$gift = 1\text{ mod(n)}$
n为奇数则m为偶数
$gift = -mn+1\text{ mod(n*n)}$
显然-mn+1为负数 而gift为正数,二者显然差一个n^2
所以$m = \frac{n^2-gift+1}{n}$
part3
比较难的CRT 第二题考到这个程度确实超模了 给大家道歉
$gift = (1+mn)(r^n)\text{ mod(nn)}$
先余n
$gift = (r^n)\text{ mod(n)}$
显然不能用费马小定理
尝试模p q
$gift = (r^{pq})\text{ mod(p)}$
$gift = (r^{pq})\text{ mod(q)}$
似乎可以做了
不妨设$d_1 = q^{-1}\text{ mod( p-1)}$
$d_2 = p^{-1}\text{ mod( q-1)}$
此时$gift^{d_1} = (r^{pqd_1}) = (r^{p(k(p-1)+1)}) = r\text{ mod(p)}$
$gift^{d_2} = (r^{pqd_2}) = (r^{q(k(q-1)+1)}) = r\text{ mod(q)}$
接下来就是CRT了 不多说
1 | |
两道更比七道强!
ezPwntools
此题十分简单,会pwntools就会做
1 | |
我们发现给定五个更新完的seed,显然这里可以解同余方程把参数爆出来,但是由于要交互512次,所以这里肯定会存在几次得到的参数有小因子的情况,只需要再写一个除小因子的脚本即可。
$x_5-x_4 = a(x_4-x_3)\text{ mod(m)}$
$x_4-x_3 = a(x_3-x_2)\text{ mod(m)}$
交叉相乘把a消掉
$(x_4-x_3)^2 = (x_5-x_4)(x_3-x_2)\text{ mod(m)}$
然后不难发现
$m | (x_4-x_3)^2 - (x_5-x_4)(x_3-x_2)$
再来一个x4321的,求gcd再消掉小因子
得到m,ab都容易得到
1 | |
ezECC
为什么这题那么烂呢,因为这题是我去年出的
当时是给冬季招新用的,结果当时一个人没做出来,想着今年给复用了。
(小故事里也提到了 冬日的战斗)
其实也是为了奖励是不是真的有复盘冬季招新的人
确实挺烂的,早知道高手这么多,我就再加个曲线映射了。
1 | |
给定域 $GF(p)$,椭圆曲线 $E_p: y^2 = x^3 + ax + b$ 上任意 $4$ 点 $A_1,A_2,A_3,A_4$,与 $e$ 倍基点 $K(m+1, y_{lift_x})$,$eK$ 的坐标,求 $m$。
对于点 $A_i(x_i, y_i)$ 有
$$y_i^2 \equiv x_i^3 + ax_i + b (\text{mod } p)$$
一样是先消去 $b$,用 $a$ 联立两个方程得到 $p$,然后解出 $a, b$。
利用 sage 自带的求椭圆曲线阶的函数 E.order(),求得阶为 $P$,这个题就转化为了:
$K$ 为椭圆曲线 $E_p$ 上一点,已知 $eK$,$e$,求 $K$。
求出 $e$ 关于阶 $P$ 的逆元即可。
1 | |
ezFakekey
这题应该能算是我的得意之作吧,有种pwn密码的美感,灵感来源于2023熵密杯初始谜题。
来源于CBC翻转,但做了一点改进。
1 | |
让我们把CBC原理搬出来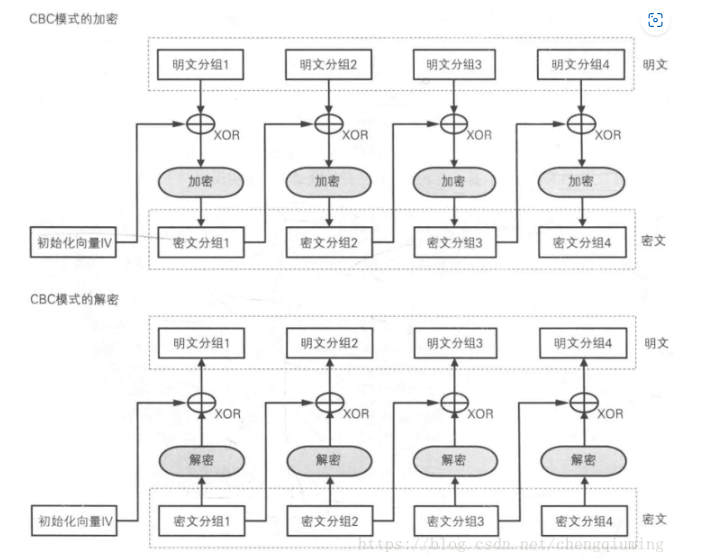 。
。
我们需要伪造密文,使得解密后存在b’Administrator’字段。
观察代码容易发现iv和key都是一样的。
怎么伪造呢
我们可以在网上搜索CBC翻转攻击,会发现关键出在异或上。
假设我们加密b’a’*32 会发现密文分组二是由明文分组一和密文分组一 异或再加密得到的。
那么反过来,如果我们已经知道了密文分组二在直接经过解密的结果(还没和密文分组一异或之前)我们可以故意构造密文分组一,达到效果。
用文字说太累了,还是写点公式吧。
我们加密b’a’*32,这部分会分为为两块,设为$pad_1$,$pad_2$.
密文分组一
$cip_1 = AES(pad_1\oplus IV)$
$cip_2 = AES(pad_2\oplus cip_1)$
想要让明文分组2为Administrator
可令$payload_1 = pad_2 \oplus cip_1 \oplus b’Administrator’$
此时$cip_2$解密完就是$(pad_2\oplus cip_1)$
和payload1异或就是b’Administrator’
看来下次得多出点这种纯密码题了,老出数学大家都思维惯性了^^.
1 | |
真的很像pwn题
后记
哎 这么快一年就过去了,追上前浪还很远,后浪却已在眼前,今年出的这么难,还是有学弟能做完(虽然有非预期),确实很厉害啊,感觉已经到我今年二月做hgame的水平了。
去年的我一个非预期,三个简单题,居然还能拿第二,有点狗屎运了现在看来。
我也得多学点东西,不能被超过才是。