2024-熵密杯-wp-Crypto
2024-熵密杯-wp-crypto
很荣幸和学长一起去银川打了这场比赛,本人主要负责前几题,主要还是靠mix学长的审计和bartleby学长的超绝推导,最后拿下二等奖第七名。
虽然最后差一点ak,但是当时就算做出来最后一题因为没血也只能拿第六,所以也没什么所谓了
也见到了我非常喜欢的糖醋小鸡块师傅!
银川连着下了四天的雨,但是羊肉很好吃。
当时去坐飞机甚至还满座升舱了,运气真好。
简单写写。
规则
当时忘记把比赛规则带出来了,印象里是三道初始谜题,然后做出来任意一道可以进入第二轮,第二轮有两条路径,flag1->flag2,flag3->flag4,必须把flag2和flag4都做出来才能到最终环节,最终环节就是一个签名的伪造,当时就是卡在最终环节一直没签上。
初始谜题1
其实说实话,熵密杯的题和一般的ctf题目非常不一样,比如我还没有见到用sympy写题面的题目。
1 | |
当时看的时候没什么感觉,感觉可能是格?后来队友提醒说这个部分明文是已知的,这才恍然大悟,可以直接解出key,然后后面就是简单的求逆的过程。
1 | |
简单解密完之后是一串字符,然后用他给的client端提交即可。
1 | |
初始谜题2
sm3长度扩展攻击,包括md类的所有散列函数都会有这种问题。
其实之前在数信杯做过这道题了,但是之前没出,保存的脚本在比赛的时候死活用不上,最后一个人熬到12点硬看源码做出来了,当时10多人出,没拿到血还是很可惜。
简单分析一下源码吧。
1 | |
大概就是说如果明文大于等于56字节就会分块,但是他的这一次的hash值是由上一块的hash值和这一块明文共同决定的。
$${hash}i = CF({hash}{i-1},{plain}_{i-1})$$
所以说如果上一块明文和上一块的hash都是已知的,那么我们可以扩展他的长度,来推断出下一块的hash以及最终的$sm3(plain)$。
题目:
1 | |
在这个题目里其实有一个要求就是counter必须递增,这看起来很难其实只需要让最后的明文是\xff*8即可。
简单上个exp:
1 | |
初始谜题3
这题就是一个lwe,但是是学长做的,后来看了发现e只有2**16,所以是完全可以爆破的。
所以把e爆破出来直接解方程就出了,当时做出来的人也很多。
1 | |
1 | |
也许密码应该优先考虑爆破?有点难绷了。
flag1
这题其实和当时2023熵密杯的第二题非常相似,但是当时直接逆回来写就出了,这一次我们死活没出,最后是爆破2**32出的,后来上的hint也提示说应该多线程爆破,最后三台电脑一起跑,大概两三分钟就出了。
题目莫得了,只有exp。
1 | |
当时不知道是不是0ops,没拿flag1就拿到flag2了,有点难绷,经典复刻了。
然后爆破就可以拿到压缩包密码,压缩包里面有第一个flag
flag2
第二个flag还挺有意思。
1 | |
这一题要求是把d2给求出来,我们知道
$s_2 = d_2 * k_3 (mod n)$
$ s_3 = d_2 * (r+k_2) (mod n)$
关键在于
1 | |
所以显然d2是可以解出来的
$(s_3-s_2)*r^{-1}=d_2(mod n)$
非常简单。
1 | |
flag3
生成一个公私钥对,用公钥注册,复制签名公钥得到的证书进行登录,但是登录用户名写 shangmibeiadmin 就能拿到 flag3。
当时是队友直接去gmssl的test.py找的一个公私钥对,现在想想还是有点难绷。
(暂无截图,大概就是一个简单的交互界面,要求给用户名和证书
flag4
然后得到一个总经理.zip,要求解开加密的流量,flag4就在流量里。
题目:
1 | |
可以发现,iv和key的生成依赖线性同余,但是如果要爆破可能的随机数种子需要爆破2**32,最后当然是狠狠的爆破了(
(爆破没什么好写的就不写了
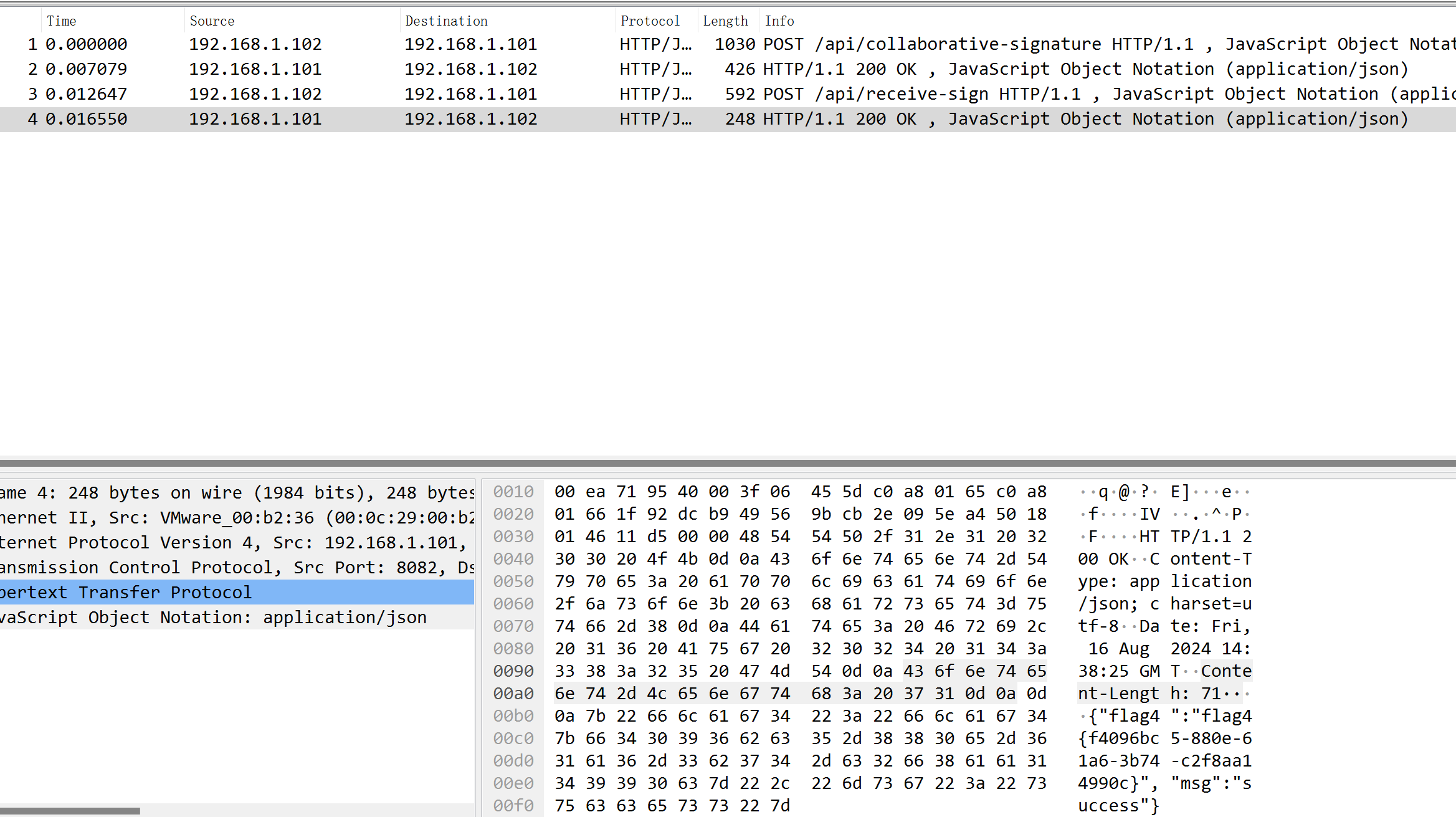
最后得到flag4
最终挑战
最终挑战,给定一个消息摘要,要求伪造总经理的签名。
其实我们有两个方程,d1和k1都是算得出来的。
1 | |
(这个结果应该是算的不对的 懒得再跑了
但是当时时间太紧,没看到用他给定的消息摘要值去伪造而是用了流量包里的。。
所以最后并没有做出来,最后的步骤大概是用给定的消息摘要值通过他的步骤去伪造这个签名,嗯。
如果后续找到别人的wp,会及时更新。